hello i’m
João Marcos Ramos
Cyber Security Enthusiast
"One machine can do the work of fifty ordinary men. No machine
can do the work of one extraordinary man."
- ELBERT HUBBARD


7+
year experience in IT
know me more
With the start of my Information Systems degree in 2018, I gradually became more focused on the IT field. Although I had always been interested in computers, the challenges and solutions presented by the course made me want to dive deeper into the area, especially because it is so broad. I began my career working as a computer instructor, which opened my eyes to how different people perceive technology in unique ways—whether it's how it's applied in social or professional environments, or how it functions at a basic level, from specific services to the most commonly used social networks. Through this experience, I realized that the field of Information Security is something that should be deeply explored, for both personal and logical reasons. That led me to pursue a postgraduate degree in Information Security, which has only strengthened my passion for technology and how it connects us all.
CyberSecurity Enthusiast
Passionate about protecting systems and data, always eager to learn and apply new security practices.
Network Lover
Fascinated by how devices communicate—dedicated to mastering network infrastructure, protocols, and traffic analysis.
Offensive Security Rookie
Beginning my journey into ethical hacking and red teaming, with a drive to understand systems by thinking like an attacker.
About my Experiencies...
I am a 28-year-old cybersecurity and IT professional with strong experience in networking, support, system automation, and business intelligence. Passionate about problem-solving, proactive work, and leadership, I bring a consistent history of contributions in IT environments.
Computer Instructor
Taught general IT classes including Office, Windows, internet use, and
design software like CorelDraw and Photoshop.
STUD CURSOS E IDIOMAS
(01/2019-03/2021)
Support Analyst
Supported digital certificate issuance and application using Java, and
managed client network setups.
RM CERTIFICADOS DIGITAIS
(04/2021-07/2021)
HelpDesk Analyst
Implemented systems, performed remote server access, proposed tech upgrades,
and conducted IT inventory.
Porttal SOLUÇÕES EM TI
(03/2022-08/2022)
IT Manager
Oversaw IT operations, managed ERP, BI rule creation, system optimizations,
and technical team coordination.
TECNO2000 IND. e COM.
(07/2021-03/2022 & 07/2022-Present)
5+
Companies Helped
25+
Project Done
100%
Curiosity and Update
1000+
hours in tech communication
why choose me
With over 7 years in IT and a growing portfolio in cybersecurity, I combine hands-on experience with technical curiosity. From Red Team tools to defensive strategies, my work is focused on real-world applications, automation, and continuous learning. I'm passionate about solving problems, improving systems, and making organizations more secure.
Learning, Creating, Automating and Improving CYBERSECURITY
Certified and Professional - Expert and Enthusiast
For Business To Have A Successful Defense Against Cyber attacks, The People, Processes, And Technology.
Security in the First Place
Thinking in security for secure.
Communicative and proactive
Searching for connections with the people beyond technology.

In cybersecurity, it's not about if you'll be targeted —
it's about when.
Be ready, stay ahead
Be Secure
MY PROJECTS
My cybersecurity projects focus on practical, real-world tools for offensive and defensive tasks. From vulnerability scanning and network mapping to data extraction and log analysis, each solution is designed with automation, ethical security, and efficiency in mind. These projects reflect my passion for problem-solving and my commitment to continuous learning in cybersecurity and Python development.
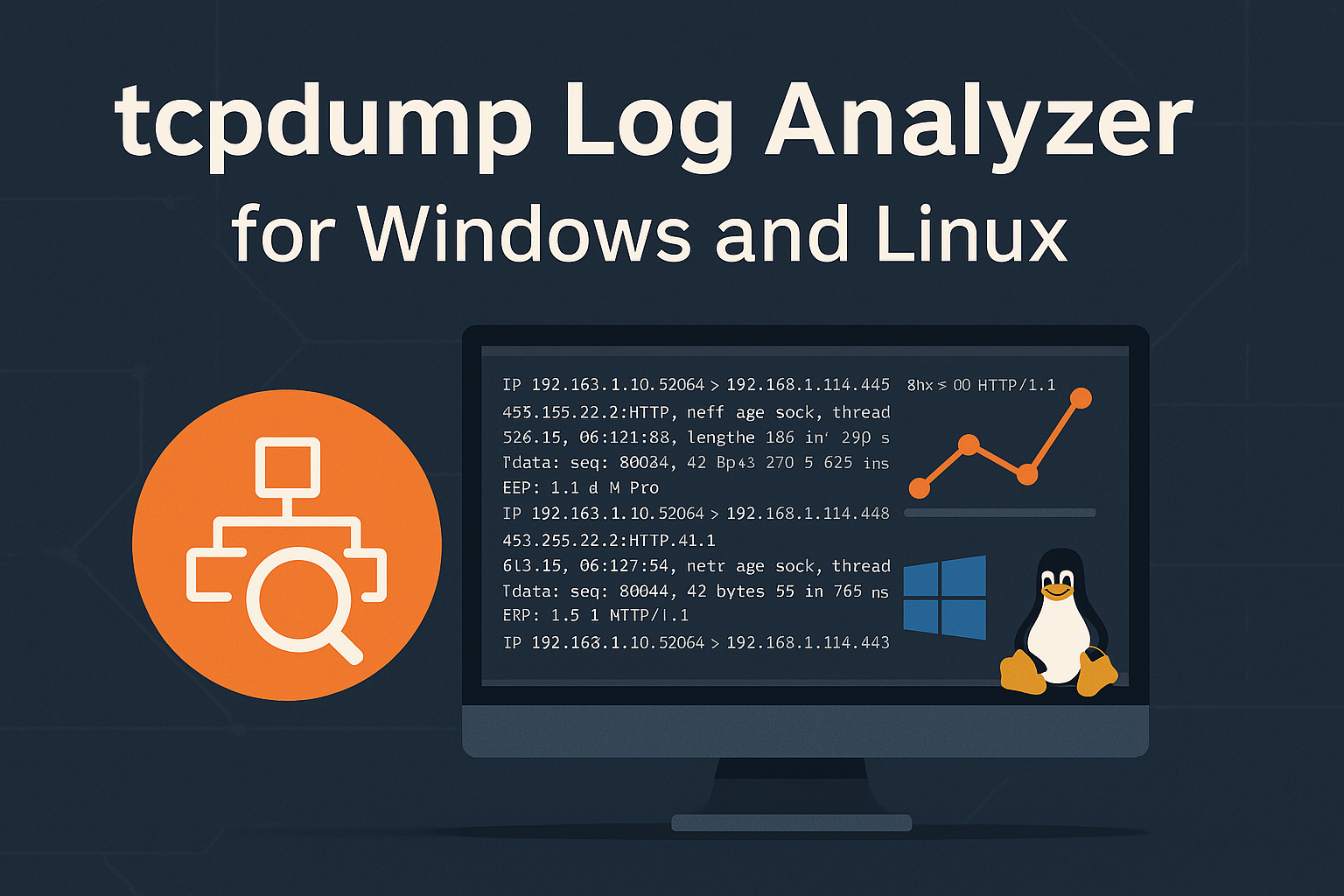
Log tcpdump Analyzer for Windows and Linux
A cross-platform Python tool that parses and analyzes tcpdump logs, extracting key network data like ports, timestamps, and protocols to help users better understand traffic patterns and detect anomalies.
Analising the Logs of the Ethernet and giving a brief
- Malware Detection Removal
- Remember To Log Off
- Shop Safety In Trusted Websites

Port Scanning with Python
Scans networks to identify open ports quickly and efficiently, providing insights into exposed services and potential entry points.
Analyze The Current Security Posture
- Malware Detection Removal
- Remember To Log Off
- Shop Safety In Trusted Websites

DNS Crawling
Scans and resolves DNS records and subdomains, helping assess the visibility and structure of a target domain from a reconnaissance perspective.
Analyze The Current Security Posture
- Malware Detection Removal
- Remember To Log Off
- Shop Safety In Trusted Websites

Network Scanning with Python
Explores devices and endpoints within a local network, gathering basic info like IPs, ports, and hostnames for situational awareness.
Analyze The Current Security Posture
- Malware Detection Removal
- Remember To Log Off
- Shop Safety In Trusted Websites

SQL Injection Detection
Identifies insecure inputs and behaviors in web applications vulnerable to SQL Injection, helping developers and analysts secure their systems.
Analyze The Current Security Posture
- Malware Detection Removal
- Remember To Log Off
- Shop Safety In Trusted Websites
Directory Finder
Traverses and logs directory structures from local storage or servers, assisting with audits, organization, and digital forensics.
Analyze The Current Security Posture
- Malware Detection Removal
- Remember To Log Off
- Shop Safety In Trusted Websites
areas of interest or expertise
I’m passionate about exploring both offensive and defensive aspects of cybersecurity. My focus includes ethical hacking, network and web application security, vulnerability scanning, log analysis, and automation with Python. I’m constantly expanding my knowledge in Red Team tactics, Blue Team defense, and real-world problem solving to build safer digital environments.
my achievements
Security Information. I've Been In The It Industry Since 2018, And In 2022 I Began To Concentrate On It CyberSecurity. Since Then, I Have Dedicate to.
Bachelor's in Information Systems
UNIS-MG (2018-2022)
Gained solid foundations in software development, databases, networking, and IT management, with a focus on applying technology to solve real-world business problems.
Postgrad in Information Security
Estácio de Sá (2022-2023)
Specialized in cybersecurity principles, risk management, data protection, and ethical hacking, preparing for strategic roles in defending digital environments.
Cybersecurity Fundamentals – Google (Coursera) (In Course)
Completing foundational training in cybersecurity concepts, including threat detection, network security, and best practices for protecting information systems—developed by Google and delivered via Coursera.
CompTIA Security+ (Training Course) (In Course)
Studied core principles of cybersecurity including network security, cryptography, risk management, and incident response—aligned with industry-standard certification objectives.
Get in touch
Expend my time in Cybersecurity...